IEEE 802 is a family of Institute of Electrical and Electronics Engineers (IEEE) standards for local area networks (LAN), personal area network (PAN), and metropolitan area networks (MAN). The IEEE 802 LAN/MAN Standards Committee (LMSC) maintains these standards. The IEEE 802 family of standards has twelve members, numbered 802.1 through 802.12, with a focus group of the LMSC devoted to each.
FileMaker Pro is a low code tool with pro code power. So, while you don't have to be a developer to make an app, if you are one, we've got you covered. Using FileMaker Pro, any problem solver can: Drag and drop to create layouts. Use built-in templates and add-ons. Run apps on Windows and Mac. Please note, after downloading and applying the FileMaker Pro 12.0v4 or FileMaker Pro 12.0v4 Advanced update on Mac OS X, you must re-start your machine before using the software. Installation instructions To ensure a smooth installation, disable virus detection software before applying the update, and re-enable it after you are finished. Download filemaker pro 12 advanced mac for free. Business tools downloads - FileMaker Pro Advanced by MacMedia and many more programs are available for instant and free download. FileMaker Pro 12.0v4 and FileMaker Pro 12.0v4 Advanced Updater FileMaker Pro 12.0v3 and FileMaker Pro 12.0v3 Advanced Updater FileMaker 12.3.103a xDBC update for FileMaker Pro and FileMaker Server. Filemaker pro 12 mac uninstall.
- Mac Protocols For High Speed Lans
- Lan Protocols List
- Mac Protocols For Language
- Lan Protocols Vs Wan Protocols
- Mac Lan Scanner
The Media Access Control (MAC) data communication Networks protocol sub-layer, also known as the Medium Access Control, is a sub-layer of the data link layer specified in the seven-layer OSI model. The medium access layer was made necessary by systems that share a common communications medium. Typically these are local area networks. The MAC layer is the 'low' part of the second OSI layer, the.
Download edrawings. The IEEE 802 standards are restricted to networks carrying variable-size packets, unlike cell relay networks, for example, in which data is transmitted in short, uniformly sized units called cells. Isochronous signal networks, in which data is transmitted as a steady stream of octets, or groups of octets, at regular time intervals, are also outside the scope of the IEEE 802 standards.
The number 802 has no significance: it was simply the next number in the sequence that the IEEE used for standards projects.[1]
The services and protocols specified in IEEE 802 map to the lower two layers (data link and physical) of the seven-layer Open Systems Interconnection (OSI) networking reference model. IEEE 802 divides the OSI data link layer into two sub-layers: logical link control (LLC) and medium access control (MAC), as follows:
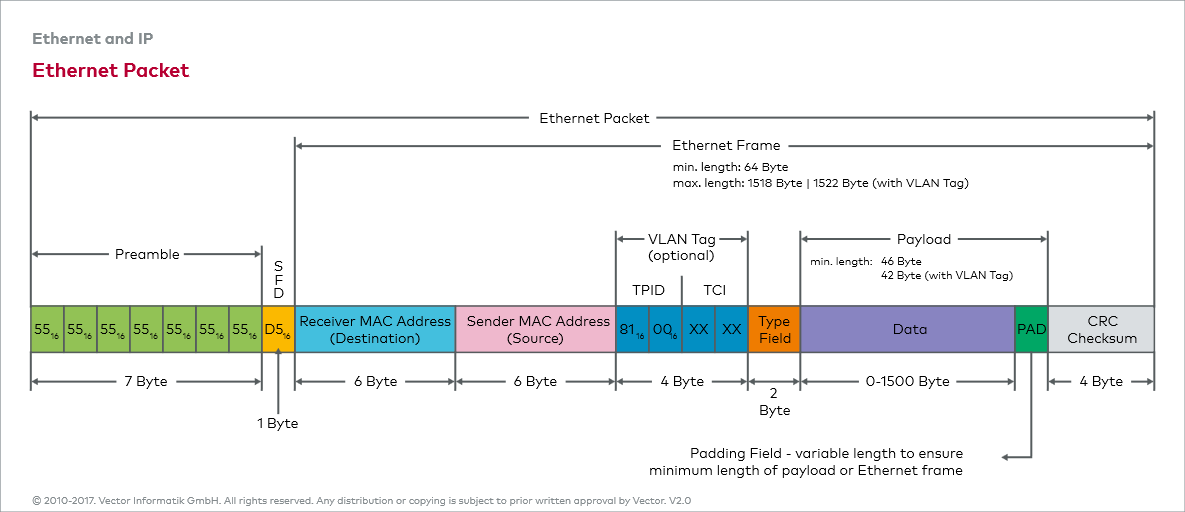
- Data link layer
- LLC sublayer
- MAC sublayer
The most widely used of these standards are for the Ethernet family, token ring, wireless network protocols (including Wi-Fi), and bridging protocols.[citation needed]
IEEE 802.11 is part of the IEEE 802 set of local area network (LAN) protocols, and specifies the set of media access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) Wi-Fi computer communication in various frequencies, including but not limited to 2.4 GHz, 5 GHz, 6 GHz, and 60 GHz frequency bands. Such network and these are nothing but only MAC protocols 4 5. In this paper is organized various protocols involve in designing MAC protocols. Ad hoc network MAC protocols can be classified into three types (Figure 1): Contention-based protocols, Contention-based protocols with. 1 MACAW: A Media Access Protocol for Wireless LAN's Abdel-Karim Al Tamimi Introduction Based on MACA, a Multiple Access Collision Avoidance protocol. Initial attempt to deal with WLAN challenges. Four key main observations: The relevant contention is at the receiver not the sender. Congestion is location dependent. Learning about the contention level must be a collective. Media Access Control has its roots in network computing under the Ethernet protocol, where it provides the data link layer for LAN systems. MAC encapsulates payload data by adding Protocol Control Information (PCI) as a 14-byte header before the information, and adding a.
Working groups[edit]
| Name | Description | Status |
|---|---|---|
| IEEE 802.1 | Higher Layer LAN Protocols Working Group | Active |
| IEEE 802.2 | LLC | Disbanded |
| IEEE 802.3 | Ethernet | Active |
| IEEE 802.4 | Token bus | Disbanded |
| IEEE 802.5 | Token ring MAC layer | Disbanded |
| IEEE 802.6 | MANs (DQDB) | Disbanded |
| IEEE 802.7 | Broadband LAN using Coaxial Cable | Disbanded |
| IEEE 802.8 | Fiber Optic TAG | Disbanded |
| IEEE 802.9 | Integrated Services LAN (ISLAN or isoEthernet) | Disbanded |
| IEEE 802.10 | Interoperable LAN Security | Disbanded |
| IEEE 802.11 | Wireless LAN (WLAN) & Mesh (Wi-Fi certification) | Active |
| IEEE 802.12 | 100BaseVG | Disbanded |
| IEEE 802.13 | Unused[2] | reserved for Fast Ethernet development[3] |
| IEEE 802.14 | Cable modems | Disbanded |
| IEEE 802.15 | Wireless PAN | Active |
| IEEE 802.15.1 | Bluetooth certification | Disbanded |
| IEEE 802.15.2 | IEEE 802.15 and IEEE 802.11 coexistence | Hibernating[4] |
| IEEE 802.15.3 | High-Rate wireless PAN (e.g., UWB, etc.) | ? |
| IEEE 802.15.4 | Low-Rate wireless PAN (e.g., ZigBee, WirelessHART, MiWi, etc.) | Active |
| IEEE 802.15.5 | Mesh networking for WPAN | ? |
| IEEE 802.15.6 | Body area network | Active |
| IEEE 802.15.7 | Visible light communications | ? |
| IEEE 802.16 | Broadband Wireless Access (WiMAX certification) | hibernating |
| IEEE 802.16.1 | Local Multipoint Distribution Service | hibernating |
| IEEE 802.16.2 | Coexistence wireless access | hibernating |
| IEEE 802.17 | Resilient packet ring | Disbanded |
| IEEE 802.18 | Radio Regulatory TAG | ? |
| IEEE 802.19 | Wireless Coexistence Working Group | ? |
| IEEE 802.20 | Mobile Broadband Wireless Access | Disbanded |
| IEEE 802.21 | Media Independent Handoff | hibernating |
| IEEE 802.22 | Wireless Regional Area Network | hibernating |
| IEEE 802.23 | Emergency Services Working Group | Disbanded |
| IEEE 802.24 | Vertical Applications TAG | ? |
See also[edit]
References[edit]
- IEEE Std 802-1990: IEEE standards for Local and Metropolitan Networks: Overview and Architecture New York:1990
- ^Institute of Electrical and Electronics Engineers (September 2004). 'Overview and Guide to the IEEE 802 LMSC'(PDF). Retrieved October 13, 2020.
- ^'802.3'. Data Communincation Standards and Protocols. EE Herald. Retrieved 2012-01-25.
- ^'The fate of 100 Mbps Ethernet now definitely two-fold'. FDDI News. Boston: Information Gatekeepers, Inc. 4 (7): 1–2. July 1993. ISSN1051-1903. Retrieved 2013-11-21.
- ^'IEEE 802.15 WPAN Task Group 2 (TG2)'. official web site. IEEE Standards Association. May 12, 2004. Retrieved June 30, 2011.
External links[edit]
- IEEE 802 Standards available via IEEE Get Program
The Data Link Layer is responsible for transmission of data between two nodes. Its main functions are-
- Data Link Control
- Multiple Access Control
Data Link control –
The data link control is responsible for reliable transmission of message over transmission channel by using techniques like framing, error control and flow control. For Data link control refer to – Stop and Wait ARQ
Multiple Access Control –
If there is a dedicated link between the sender and the receiver then data link control layer is sufficient, however if there is no dedicated link present then multiple stations can access the channel simultaneously. Hence multiple access protocols are required to decrease collision and avoid crosstalk. For example, in a classroom full of students, when a teacher asks a question and all the students (or stations) start answering simultaneously (send data at same time) then a lot of chaos is created( data overlap or data lost) then it is the job of the teacher (multiple access protocols) to manage the students and make them answer one at a time.
Thus, protocols are required for sharing data on non dedicated channels. Multiple access protocols can be subdivided further as –
1. Random Access Protocol: In this, all stations have same superiority that is no station has more priority than another station. Any station can send data depending on medium's state( idle or busy). It has two features:
- There is no fixed time for sending data
- There is no fixed sequence of stations sending data

The Random access protocols are further subdivided as:
(a) ALOHA – It was designed for wireless LAN but is also applicable for shared medium. In this, multiple stations can transmit data at the same time and can hence lead to collision and data being garbled.
- Data link layer
- LLC sublayer
- MAC sublayer
The most widely used of these standards are for the Ethernet family, token ring, wireless network protocols (including Wi-Fi), and bridging protocols.[citation needed]
IEEE 802.11 is part of the IEEE 802 set of local area network (LAN) protocols, and specifies the set of media access control (MAC) and physical layer (PHY) protocols for implementing wireless local area network (WLAN) Wi-Fi computer communication in various frequencies, including but not limited to 2.4 GHz, 5 GHz, 6 GHz, and 60 GHz frequency bands. Such network and these are nothing but only MAC protocols 4 5. In this paper is organized various protocols involve in designing MAC protocols. Ad hoc network MAC protocols can be classified into three types (Figure 1): Contention-based protocols, Contention-based protocols with. 1 MACAW: A Media Access Protocol for Wireless LAN's Abdel-Karim Al Tamimi Introduction Based on MACA, a Multiple Access Collision Avoidance protocol. Initial attempt to deal with WLAN challenges. Four key main observations: The relevant contention is at the receiver not the sender. Congestion is location dependent. Learning about the contention level must be a collective. Media Access Control has its roots in network computing under the Ethernet protocol, where it provides the data link layer for LAN systems. MAC encapsulates payload data by adding Protocol Control Information (PCI) as a 14-byte header before the information, and adding a.
Working groups[edit]
| Name | Description | Status |
|---|---|---|
| IEEE 802.1 | Higher Layer LAN Protocols Working Group | Active |
| IEEE 802.2 | LLC | Disbanded |
| IEEE 802.3 | Ethernet | Active |
| IEEE 802.4 | Token bus | Disbanded |
| IEEE 802.5 | Token ring MAC layer | Disbanded |
| IEEE 802.6 | MANs (DQDB) | Disbanded |
| IEEE 802.7 | Broadband LAN using Coaxial Cable | Disbanded |
| IEEE 802.8 | Fiber Optic TAG | Disbanded |
| IEEE 802.9 | Integrated Services LAN (ISLAN or isoEthernet) | Disbanded |
| IEEE 802.10 | Interoperable LAN Security | Disbanded |
| IEEE 802.11 | Wireless LAN (WLAN) & Mesh (Wi-Fi certification) | Active |
| IEEE 802.12 | 100BaseVG | Disbanded |
| IEEE 802.13 | Unused[2] | reserved for Fast Ethernet development[3] |
| IEEE 802.14 | Cable modems | Disbanded |
| IEEE 802.15 | Wireless PAN | Active |
| IEEE 802.15.1 | Bluetooth certification | Disbanded |
| IEEE 802.15.2 | IEEE 802.15 and IEEE 802.11 coexistence | Hibernating[4] |
| IEEE 802.15.3 | High-Rate wireless PAN (e.g., UWB, etc.) | ? |
| IEEE 802.15.4 | Low-Rate wireless PAN (e.g., ZigBee, WirelessHART, MiWi, etc.) | Active |
| IEEE 802.15.5 | Mesh networking for WPAN | ? |
| IEEE 802.15.6 | Body area network | Active |
| IEEE 802.15.7 | Visible light communications | ? |
| IEEE 802.16 | Broadband Wireless Access (WiMAX certification) | hibernating |
| IEEE 802.16.1 | Local Multipoint Distribution Service | hibernating |
| IEEE 802.16.2 | Coexistence wireless access | hibernating |
| IEEE 802.17 | Resilient packet ring | Disbanded |
| IEEE 802.18 | Radio Regulatory TAG | ? |
| IEEE 802.19 | Wireless Coexistence Working Group | ? |
| IEEE 802.20 | Mobile Broadband Wireless Access | Disbanded |
| IEEE 802.21 | Media Independent Handoff | hibernating |
| IEEE 802.22 | Wireless Regional Area Network | hibernating |
| IEEE 802.23 | Emergency Services Working Group | Disbanded |
| IEEE 802.24 | Vertical Applications TAG | ? |
See also[edit]
References[edit]
- IEEE Std 802-1990: IEEE standards for Local and Metropolitan Networks: Overview and Architecture New York:1990
- ^Institute of Electrical and Electronics Engineers (September 2004). 'Overview and Guide to the IEEE 802 LMSC'(PDF). Retrieved October 13, 2020.
- ^'802.3'. Data Communincation Standards and Protocols. EE Herald. Retrieved 2012-01-25.
- ^'The fate of 100 Mbps Ethernet now definitely two-fold'. FDDI News. Boston: Information Gatekeepers, Inc. 4 (7): 1–2. July 1993. ISSN1051-1903. Retrieved 2013-11-21.
- ^'IEEE 802.15 WPAN Task Group 2 (TG2)'. official web site. IEEE Standards Association. May 12, 2004. Retrieved June 30, 2011.
External links[edit]
- IEEE 802 Standards available via IEEE Get Program
The Data Link Layer is responsible for transmission of data between two nodes. Its main functions are-
- Data Link Control
- Multiple Access Control
Data Link control –
The data link control is responsible for reliable transmission of message over transmission channel by using techniques like framing, error control and flow control. For Data link control refer to – Stop and Wait ARQ
Multiple Access Control –
If there is a dedicated link between the sender and the receiver then data link control layer is sufficient, however if there is no dedicated link present then multiple stations can access the channel simultaneously. Hence multiple access protocols are required to decrease collision and avoid crosstalk. For example, in a classroom full of students, when a teacher asks a question and all the students (or stations) start answering simultaneously (send data at same time) then a lot of chaos is created( data overlap or data lost) then it is the job of the teacher (multiple access protocols) to manage the students and make them answer one at a time.
Thus, protocols are required for sharing data on non dedicated channels. Multiple access protocols can be subdivided further as –
1. Random Access Protocol: In this, all stations have same superiority that is no station has more priority than another station. Any station can send data depending on medium's state( idle or busy). It has two features:
- There is no fixed time for sending data
- There is no fixed sequence of stations sending data
The Random access protocols are further subdivided as:
(a) ALOHA – It was designed for wireless LAN but is also applicable for shared medium. In this, multiple stations can transmit data at the same time and can hence lead to collision and data being garbled.
Mac Protocols For High Speed Lans
- Pure Aloha:
When a station sends data it waits for an acknowledgement. If the acknowledgement doesn't come within the allotted time then the station waits for a random amount of time called back-off time (Tb) and re-sends the data. Since different stations wait for different amount of time, the probability of further collision decreases. - Slotted Aloha:
It is similar to pure aloha, except that we divide time into slots and sending of data is allowed only at the beginning of these slots. If a station misses out the allowed time, it must wait for the next slot. This reduces the probability of collision.
For more information on ALOHA refer – LAN Technologies
(b) CSMA – Carrier Sense Multiple Access ensures fewer collisions as the station is required to first sense the medium (for idle or busy) before transmitting data. If it is idle then it sends data, otherwise it waits till the channel becomes idle. However there is still chance of collision in CSMA due to propagation delay. For example, if station A wants to send data, it will first sense the medium.If it finds the channel idle, it will start sending data. However, by the time the first bit of data is transmitted (delayed due to propagation delay) from station A, if station B requests to send data and senses the medium it will also find it idle and will also send data. This will result in collision of data from station A and B.
Mac app for developers iphone. IOS matches the Invocation URL against URLs that you registered as a part of your App Clip Experience.
CSMA access modes-
- 1-persistent: The node senses the channel, if idle it sends the data, otherwise it continuously keeps on checking the medium for being idle and transmits unconditionally(with 1 probability) as soon as the channel gets idle.
- Non-Persistent: The node senses the channel, if idle it sends the data, otherwise it checks the medium after a random amount of time (not continuously) and transmits when found idle.
- P-persistent: The node senses the medium, if idle it sends the data with p probability. If the data is not transmitted ((1-p) probability) then it waits for some time and checks the medium again, now if it is found idle then it send with p probability. This repeat continues until the frame is sent. It is used in Wifi and packet radio systems.
- O-persistent: Superiority of nodes is decided beforehand and transmission occurs in that order. If the medium is idle, node waits for its time slot to send data.
(c) CSMA/CD – Carrier sense multiple access with collision detection. Stations can terminate transmission of data if collision is detected. For more details refer – Efficiency of CSMA/CD
(d) CSMA/CA – Carrier sense multiple access with collision avoidance. The process of collisions detection involves sender receiving acknowledgement signals. If there is just one signal(its own) then the data is successfully sent but if there are two signals(its own and the one with which it has collided) then it means a collision has occurred. To distinguish between these two cases, collision must have a lot of impact on received signal. However it is not so in wired networks, so CSMA/CA is used in this case.
CSMA/CA avoids collision by:
- Interframe space – Station waits for medium to become idle and if found idle it does not immediately send data (to avoid collision due to propagation delay) rather it waits for a period of time called Interframe space or IFS. After this time it again checks the medium for being idle. The IFS duration depends on the priority of station.
- Contention Window – It is the amount of time divided into slots. If the sender is ready to send data, it chooses a random number of slots as wait time which doubles every time medium is not found idle. If the medium is found busy it does not restart the entire process, rather it restarts the timer when the channel is found idle again.
- Acknowledgement – The sender re-transmits the data if acknowledgement is not received before time-out.
2. Controlled Access:
In this, the data is sent by that station which is approved by all other stations. For further details refer – Controlled Access Protocols
3. Channelization:
In this, the available bandwidth of the link is shared in time, frequency and code to multiple stations to access channel simultaneously.
Lan Protocols List
- Frequency Division Multiple Access (FDMA) – The available bandwidth is divided into equal bands so that each station can be allocated its own band. Guard bands are also added so that no to bands overlap to avoid crosstalk and noise.
- Time Division Multiple Access (TDMA) – In this, the bandwidth is shared between multiple stations. To avoid collision time is divided into slots and stations are allotted these slots to transmit data. However there is a overhead of synchronization as each station needs to know its time slot. This is resolved by adding synchronization bits to each slot. Another issue with TDMA is propagation delay which is resolved by addition of guard bands.
For more details refer – Circuit Switching - Code Division Multiple Access (CDMA) – One channel carries all transmissions simultaneously. There is neither division of bandwidth nor division of time. For example, if there are many people in a room all speaking at the same time, then also perfect reception of data is possible if only two person speak the same language. Similarly data from different stations can be transmitted simultaneously in different code languages.
Mac Protocols For Language
Attention reader! Don't stop learning now. Get hold of all the important CS Theory concepts for SDE interviews with the CS Theory Course at a student-friendly price and become industry ready.
Recommended Posts:
If you like GeeksforGeeks and would like to contribute, you can also write an article using contribute.geeksforgeeks.org or mail your article to contribute@geeksforgeeks.org. See your article appearing on the GeeksforGeeks main page and help other Geeks.
Lan Protocols Vs Wan Protocols
Please Improve this article if you find anything incorrect by clicking on the 'Improve Article' button below.
